Elaborating below, some of the major areas that I have been working on in the last couple of years. I have also included any CTF’s styled events that I have taken part in the last couple of years. I am still a year into infosec, and if you are someone who wants to work on something similar or different in technology/ infosec, shoot me an email or contact me at LinkedIn or Github .
1. CyberMetrics
August 2019 - December 2019 under Professor Edward Amoroso
Quantifying cyber risk is one of the biggest challenges in info sec today. Since the advent of the Orange book, people have been trying to quantify security or measure it in some form. Does the phrase “less” or “more secure” have any inference ? Though security may never be directly measured, can there be some metrics for it. There are various frameworks, and organizations such as PCI-DSS, NIST standards, BSIMM which focuses on software security.
This endeavour of cyber metrics done by the research team at NYU asks the question whether a reliable metrics of cyber metrics can be formed by asking the gut feeling of cybersecurity experts.
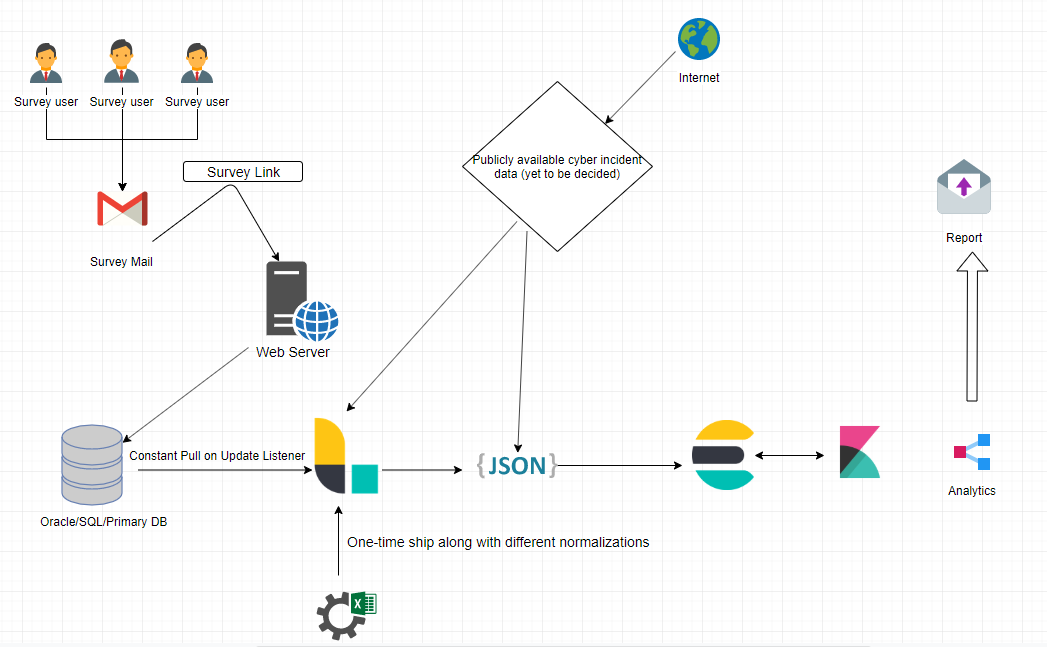
NYU’s cyber metrics index of expert opinion or “gut feeling” on status of cyber security has been collecting opinion data over the last 8 years. This is an attempt to parse through and analyze the data with the ELK stack and conclude whether any corelations can be drawn between “gut feeling of experts” and “the actual state of cyber security”.
A part of a team of 6 students in the Fall semester, working to find relation between various aspects of the data collected by survey started 8 years back by Dan Geer and Mukul Pareek.
I worked on setting up the pipeline for pulling in the data, setting up a planned infrastructure for easier ingesting of data, and corelating the existing with various publicly available data related to cybersecurity breach, released CVE’s to find patterns if any and aid in research work towards the technical paper on NYU’s Cyber Index.
2. Implementing Network Security Monitoring
July 2019 - December 2019 under Professor Thomas Reddington
Network security is a complex process involving a lot of different micro components that need to be fine tuned to orchestrate a smooth, fast , adaptive and scalable implementation. For an organization to have a hardened NSM model, it must go through thorough and rigourous designs, redesigns and reviews before arriving at an optimal implementation. The dynamic nature of the threat that a network faces adds to the challenge of the task at hand, and an organization must either outsource or have a dedicated team of professionals in this area who are continously trained to maintain the NSM and modify it when the need be. The Application Collection Framework and Collective Intelligence frameworks are some which provide good reference points in setting up NSM for a given network. From deciding sensor hardware and placement, to deciding algorithms that detect threats faster, to building a scalable architecture that can adapt to changes well- A network security analyst is expected to know a vast array of skills proficiently.
Technologies Used:
- Justniffer, Zeek for PTSR data extraction
- YAF, SiLK (Cert NetSA tools) for flow collection and generation
- GNS3 For Network Simulation
- Security Onion as a reference Sensor
- Bash scripts for various tasks such as monitoring, logging, and miscellaneous other automations
- Filebeat for shipping logs
- FRR as router software
- Application Collection Framework /Collection Intelligence Framework as guidance
- Logstash for centrally collecting and transferring logs
- Elasticsearch for distributed storage of logs.
- Kibana for visual analysis of logs.
- Ansible for managing multiple nodes in the network
- Python for automation.
The full project can be found here: Github Link . I am still continuing work in this area, if you have similar interests would be happy to collaborate. The whitepaper on the same can be found here:> Pdf link
3. Relevant Academic Coursework:
Penetration Testing and Vulnerability Analysis: Case Studies
- Spectre and Meltdown: A scenario based MLA styled report which is written as a demonstrated communication between a security team of a company to the other teams and upper management explaining them the vulnerability Spectre and Meltdown and the impact to the organization, and measures that need to be taken. View the full pdf report .
- MS08-067 Case study: A scenario based MLA styled report written as a demonstrated communication between the security team of the company to other teams such as developer and upper management explaining the vulnerability to them and the impact towards the organization and measures that need to be taken. View the full pdf report .
- Vehicle Hacking: Case study: An MLA styled report explaining the vehicle hacking which was presented by Dr Charlie Miller and Chris Valasek on how a vehicle may be remotely hacked into. The security team explains the impact to the other teams of the hypothetical organization. View the full pdf report.
Cyber Range Lab: Penetration Testing and Vulnerability analysis final project.
The final project of the course was to simulate a penetration testing scenario on company from breaking physical security to breaking into machines, and documenting the penetration testing work in a OSCP styled professional Pentesting report. It was a good window to the world of real world pentesting and a befitting final project to end the course. The full report can be viewed here :