Dynamic Linked Lists
Simply put, dynamic linked libraries are external libraries which are needed by a program during run time. There are different kinds of DLL’s and are treated differently by the operating system as such. The APP_INIT DLL’s are known trusted DLL’s which are loaded from the registry before Any process starts (Except the logon process) such as rundll32. The exploits related to AppInit DLL require the corruption or manipulation of known dll’s in the registry and will be covered in a later post.
How does a DLL work ?
Many functions are called by the dll,some of which are exportable. There is an optional main function which dll implements if it wants to do any startup activity. The things we can do within this Main function is restricted (We cannot load another DLL as we shall see).
An exe loads DLL from disk using LoadLibraryFunction , finds appropriate function by using GetProcAddress. These 2 functions are extremely important as LoadLibrary loads the DLL, and GetProcAddress is the first instance where the DLL calls another function. The 2 kinds of DLL’s are as under.
- System DLL's : barebones basic functions that dll requires, winsock dll (eg Basic connection), kernel32 dll.
- Application DLL's : These are custom dll that ship with applications. We may have encountered common missing DLL while trying to load our favorite games.These DLL files are programmed by the developers of the application.
The next thing to understand is how DLL’s are loaded into a given program. If an exe is going through the process going with the function loader. Default DLL search order comes into play. This mechanism of search order is not new to attackers and has been the target for exploits for a long time. I suggest reading more into this, which I too am doing. Safe DLL search came in from Windows XP SP2 onwards, when DLL hijacking became sort of rampant. This mechanism stops some DLL hijacking attacks but far from being exploit proof. This blog on the microsoft website explains how a given DLL is searched. MSDN Link.
Loading meterpreter reverse shell from the infected DLL’s using DLLMain?
There is a custom stager of meterpreter for DLL written by Raphael Mudge which we can use. The code snippet for the DLLMain function is pasted below. It is a 64 bit version, which has been modified from the original 32 bit version. The full link for the code can be found here As an attacker, aim would be to create a reverse shell , connectg back to the attacker. Load the stage2 metasrv.dll and stdapi to spawn a full fledge meterpreter shell with stdapi. As we see however trying to do this fails. You can try this on your own, but the stage 2 of the meterpreter will not load as there are restrictions on the things we can do from DLL Main. See the stackoverflow blog for details Link.
Alternative?
Since we have already estabilished that we cannot load the metsrv.dll from the DLL Main, what we can do is make the victim program call our function which has the shellcode. We need to identify a function which is being called at an appropriate position in the DLL and then modify the name of the malicious function to be that function. Once this is done, the malicious dll will be loaded in the stable position where it can listen back to the attacker machine.
How do we do that? What are the prerequisites? Let us address each issue step by step.
- First we need a vulnerable software- A Software that is vulnerable to DLL hijacking. For this demo we will use uTorrent. This can be downloaded from exploitdb at this link
- Suppose we don't know that plugin_dll is vulnerable, how do we figure out a list of DLL files which we want to target? We must target those DLL files which are not found by the program after going thorugh the search order, and then cause the dll file to be delivered on the same place where the executable is present.
- To find out which DLL files a program is trying to load but can't we will use something called ProcMon(Download it here link). You are free to use other tools which you deem fit. What we want to do here is to figure out which DLL's are not being requested but not found by the vulnerable uTorrent software.
-
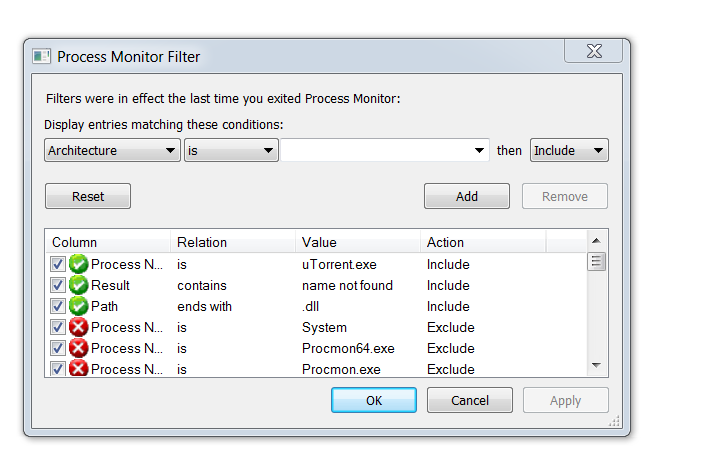
The screenshot below shows what ProcMon shows us. We need to setup filters where we feel that procmon
After applying the filters we can see that the dll's which fail to load.
-
The key point is to identify DLL's which load after the uTorrrent has just loaded into the memory.SO not all missing DLL files are viable candidates. It also reveals the search order for the DLL's used by the uTorrent application
-
utorrent.exe is packed with a packer called Upx. How did I get that information? Well, when you try to load it into IDA for analysis we get a message which lets us know it has been packed. Using a tool called "PE-Explorer" we can find out that the binary has been packed using UPX from the header. After we unpack it using-
upx -d uTorrent.exe
- IDA is a popular disassembler for windows. The IDA is available in free and commercial versions. It can be downloaded from the IDA website. The principles behind it however will remain the same. You need to know how to do basic stuff in the GUI such as insert a break point.
-
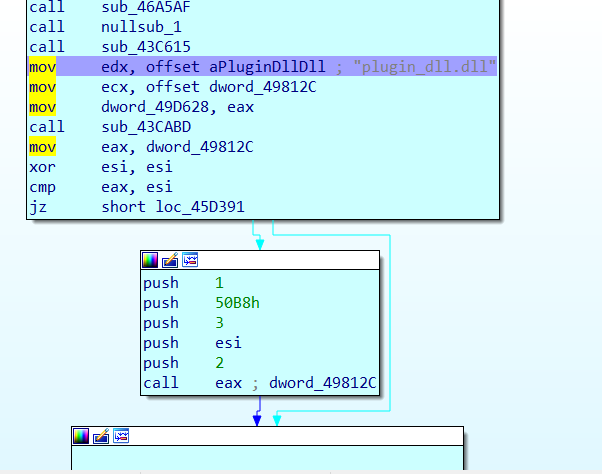
We need to search for the vulnerable dll file which is "plugin_dll.dll" through the disassembly.Once this is done we identify the string in a non ".data" section, we identify the subroutine just after this. See the image below for reference. The red line was the place where we inserted the breakpoint.
-
Next we need to modify flags to arrive at a position which is between our dynamic duo.
The dynamic duo which is GetProcAddess and LoadLibrary . Once we do that we find that the function we need to target is loaded into the ESP register.
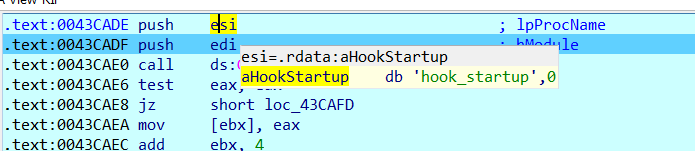
- The process name is hook_startup. Hence if we modify our to just place a function of this name in the DLL. Then if the DLL gets loaded by the function, uTorrent will call the function internally (as observed in IDA). We do not need to do a thing , and we will get the Shell. Use the code snippet below, for reference.
-
Compile the C file as a DLL using the command.
i686-w64-mingw32-gcc uTorrent-14726.c -o plugin_dll.dll -shared -lws2_32
Make sure the DLL is in the windows 7 directory with the uTorrent. -
Startup a meterpreter reverse shell on your machine and have it listen for a reverse shell from. Place the infected DLL on the directory of uTorrent.exe and start the application and notice what happens. Voila! We get a meterpreter session.
If you do not know how meterpreter works or loads shells, there is a good blog on rapid7 , the awesome developers of the famous pentesting tool , Metasploit. Link I would cover how metasploit staging works, stageless payloads and staged payloads in a future blogpost regarding Metasploit. I am still a newbie at Metasploit, hence will blog about it when I have made quantifiable progress.